
Consultation
Why choose TECHSAJ for consulting?
- Mitigate security risks with threat intelligence that delivers the latest information about cyber threats.
- Benefit from experience-driven customizable solutions that align with your unique cybersecurity needs.
- Ensure complete protection of sensitive data with cybersecurity insurance from a premier provider.
- Make informed decisions about network security with actionable insight that saves you time and money.
- Maintain your budget with cost-effective all-inclusive pricing that only bills you for necessary services.
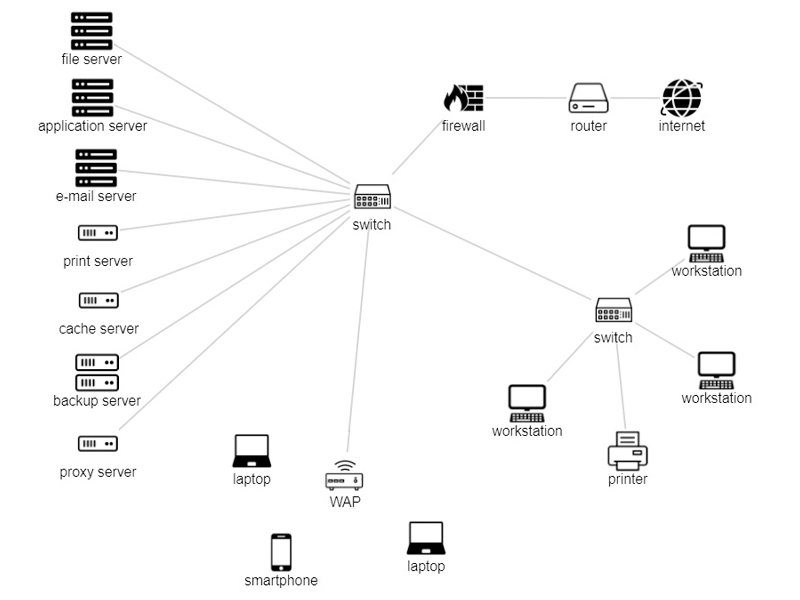
Designing
TECHSAJ Providing security strategies that cover all parts of complicated network is difficult task in network design. IT Security design is highly challenged by the complex modern networks that include a corporate network with internet and extranet access, VPN networks, public web servers for e-commerce, intranet applications, and remote-access services for users reaching the network from office, cyber cafe, home, college and so on. TECHSAJ approaches the designing requirements in a systematic way.
Following steps explains detail plan & steps to achieve security strategies:
- Understand existing network architecture.
- Understand tactical and strategic business needs in terms of IT growth.
- Identify vulnerabilities in various network assets.
- Analyze security risks resulting into business risks.
- Create a customized security plan.
- Design security solutions comprising of products and processes.
- Implement designed solutions.
- Developing plan of technical implementation.

Integration
Our integration service deploys your network security solution quickly and efficiently whilst minimizing the exposure to threats. During the Integration phase, we will incorporate some of our world class partner technologies with your existing & new technologies. This seamless integration will be carried out quickly and efficiently to minimize disruption and exposure.
We have significant expertise in the delivery of Network Access Control, Firewall Solutions, Intrusion Prevention/Intrusion Detection, Access Control, Security Event Correlation and Security Event Management Solutions.
We have extensive experience in the area of retro-fitting existing network environments to improve security posture, for example to ensure compliance with PCI standards or organisational policy. All projects are delivered using tried and trusted methodologies such as the unique Life cycle Services approach to help ensure service excellence.

Project Management.
Managing security projects is a delicate activity due to the evolution of attacks. In this paper, we develop a new methodology for estimating security effort based on algebraic representation of security policies. This methodology is used within the SECOMO model. Two models are defined: the a priori model and the a posteriori model. Real security projects are used to prove the accuracy of the new methodology.
Protecting the critical infrastructure, application estate, and company data is a massive responsibility that is much bigger than IT and cyber security. Technical teams are challenged with having a fundamental understanding of security programs. They are also challenged by the increasing number of moving people, parts, and processes around vulnerability management. Then there are security patches and a wide range of best practices required to support hybrid working from any device.

Maintenance
Any network issues are quickly identified and addressed by our expertise and understanding, means resulting in minimal disruption and cost savings. Rather than wanting ‘one throat to choke’ – you’ll want one hand to shake. And we’re right where you are. We offer you predictable costs and a framework for efficient resource allocation through a choice of traditional 24/7 support, E-Support and service automation.
This is more than a simple break-fix service. We’ll help ensure you meet network demands with the right mix of technical and operational support, keeping your network running reliably and protecting your investment. Our highly skilled and certified technicians boast extensive expertise in managing multi-platform and multi-vendor ecosystems. No matter what your environment, Algort knows how it works










